Threats on the World Wide Web
Cybersecurity focuses on the dangers and risks posed by information and communications technology. In the worst case, vulnerabilities in these IT systems can lead to sensitive data falling into the wrong hands or even being exploited for criminal activities. An effective cybersecurity strategy is needed to prevent this from happening. However, the rapid development of artificial intelligence in particular is creating new and more complex cyberattacks against which companies must take additional precautions.
Be one step ahead of hackers
Cyberthreats are manifold: from the classic hacker, who exploits the vulnerabilities and errors of a software system for their own purposes, to programmed bots, which can move around a network autonomously and spy on data. Installing an appropriate virus scanner is a crucial step in protecting against these threats, but it's far from enough. System vulnerabilities aren't the only things being exploited. Nowadays, cybercriminals also direct their attacks against the users themselves. Whether it's phishing, spoofing or spreading malware - only those companies that sensitize their employees to threats can establish a successful and long-term cybersecurity strategy.
Cybersecurity strategies and tools
Effective defense strategies are essential in today's corporate environment. Companies can leverage both technical and organizational measures to create a comprehensive security plan. Secure IT infrastructures coupled with trained employee behavior is critical to the security program's success. Only by addressing system vulnerabilities and teaching employees how to properly handle data, passwords and sensitive information can companies successfully mitigate cyberattacks.
At the same time, it's also important to prepare for the worst-case scenario. No company can protect itself from all types of cyberattacks. Incident response plans document the course of action if a successful attack does occur. Only a quick and coordinated response to such incidents can minimize the impact and limit the damage.
Everything on cybersecurity in one template
Get the most pertinent information on the latest cybersecurity topics in our updated PowerPoint template. Present the current threat landscape, the role of artificial intelligence and explain to your employees the cyberattacks they can protect themselves from and how. With our template, you'll be able to create and deliver a comprehensive and engaging presentation on cybersecurity. Use our information to emphasize the importance of an effective defense strategy and illustrate what role your employees play in it.
With the Cybersecurity Template for PowerPoint, you can
- present the current threat landscape with up-to-date statistics.
- explain the most critical types of cyberattacks and corresponding protective measures.
- raise awareness among your employees about the importance of a cybersecurity strategy.
This PowerPoint template includes:
- Quote
- Why is cybersecurity important?
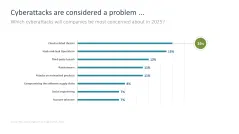
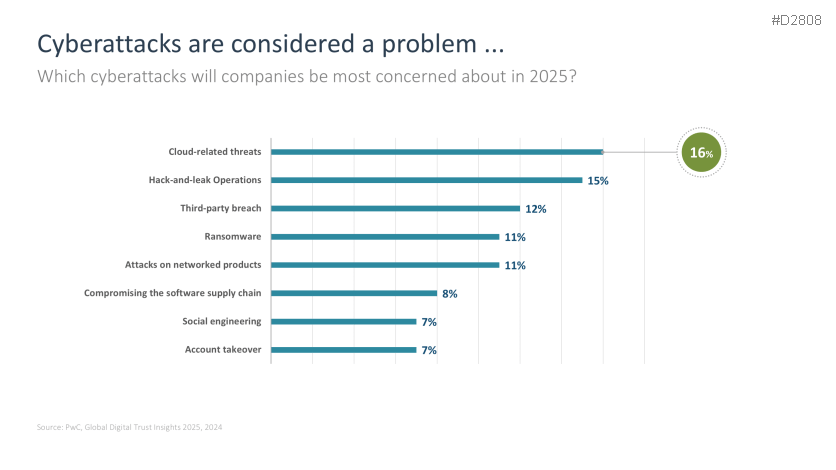
- Cyberattacks are considered a problem…
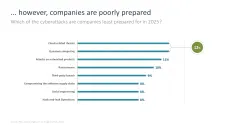
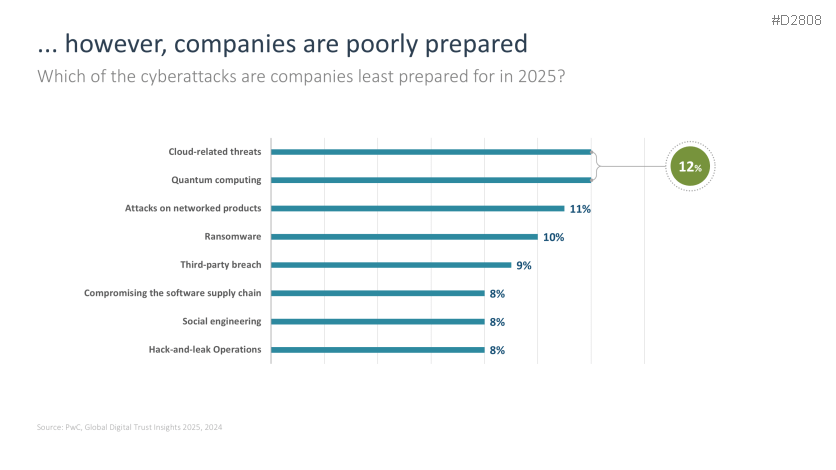
- …but companies underestimate their own risk
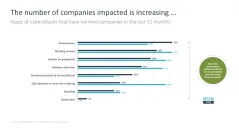
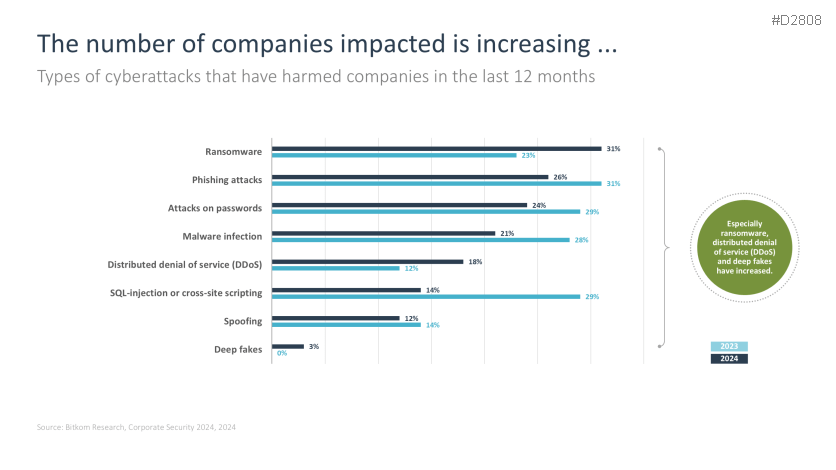
- The number of companies impacted is also rising…
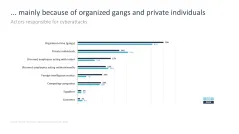
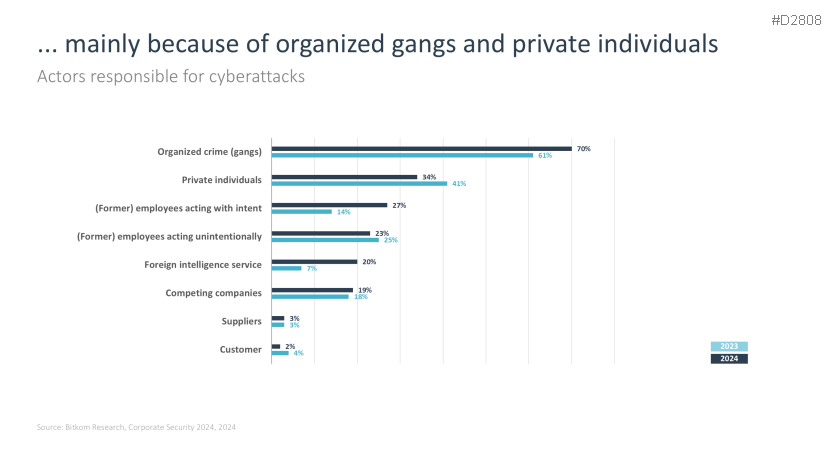
- ...through attacks by individuals and employees
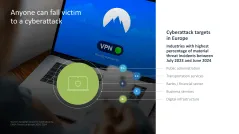
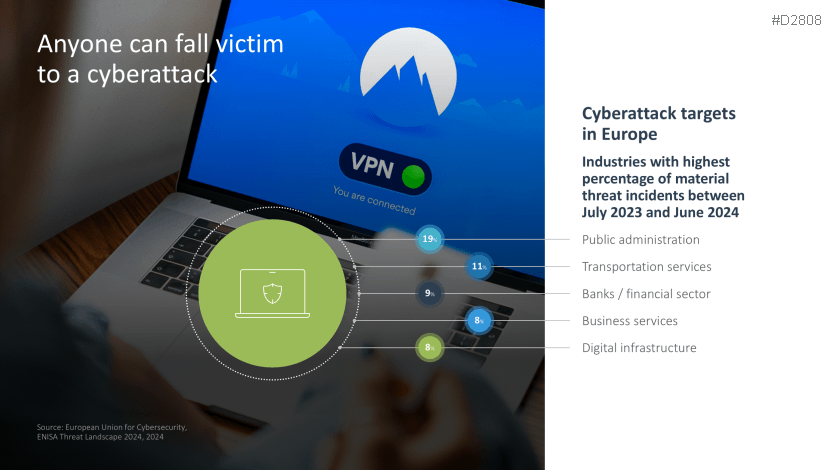
- Anyone can fall victim to a cyberattack
- Recent cyberattacks in Germany
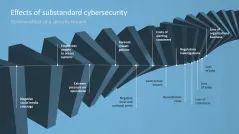
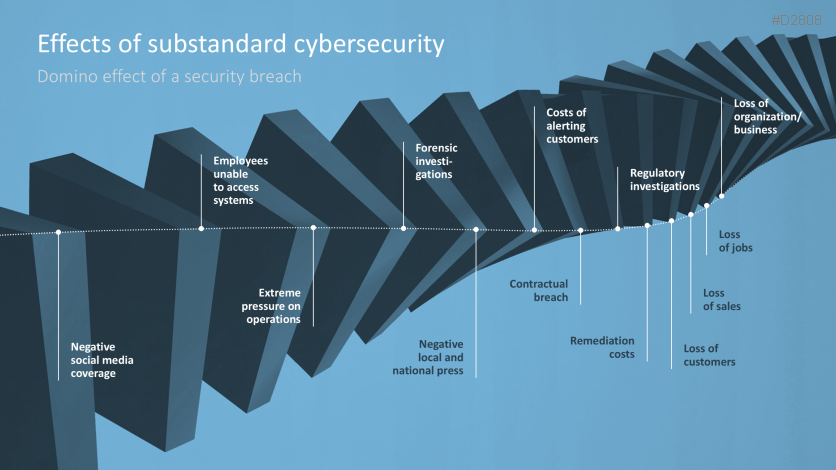
- Effects of substandard cybersecurity
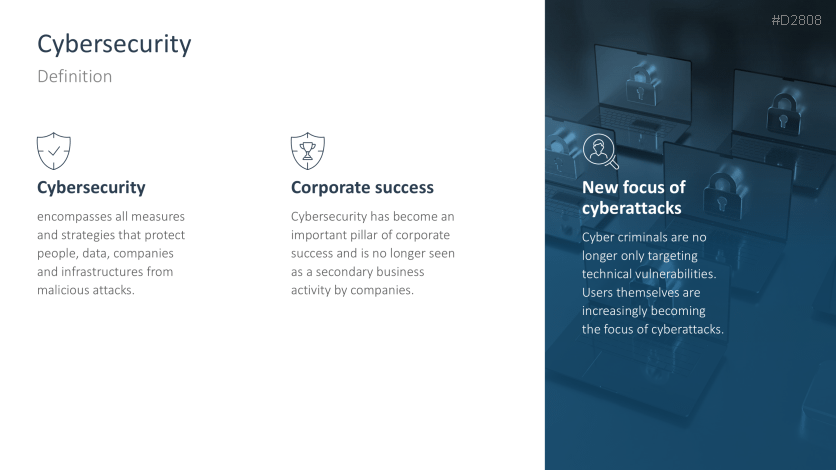
- What is cybersecurity?
- Definition
- Cybersecurity categories
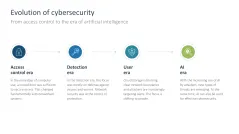
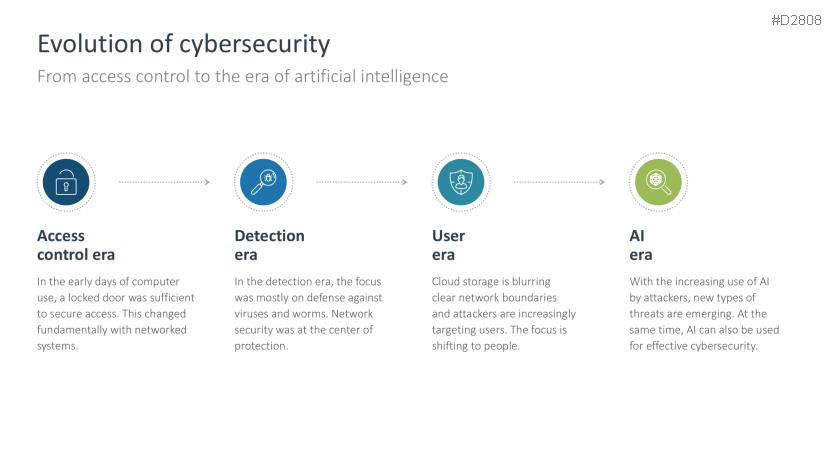
- Evolution of cybersecurity
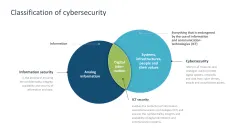
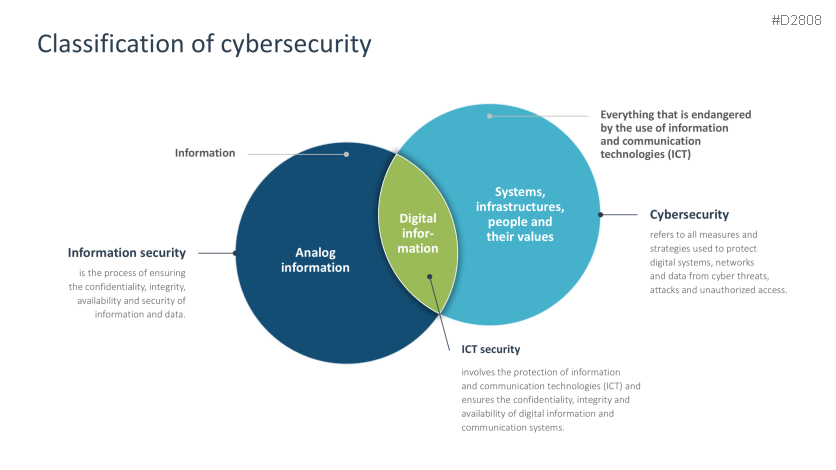
- Cybersecurity: classification
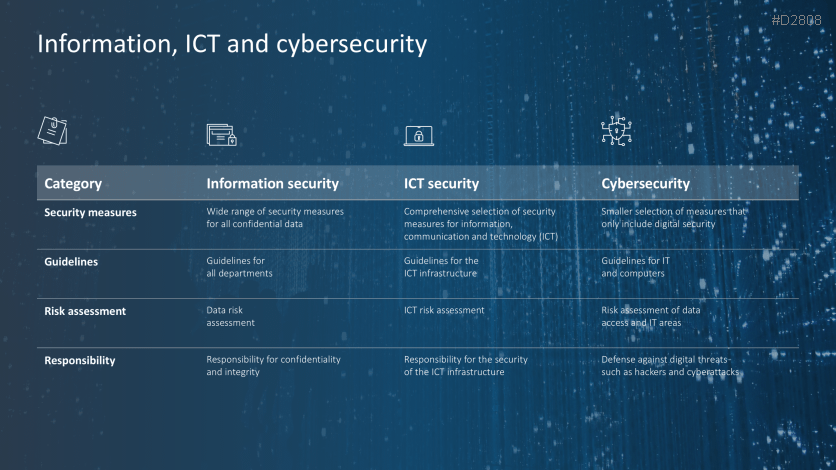
- Cybersecurity, information and ICT Security
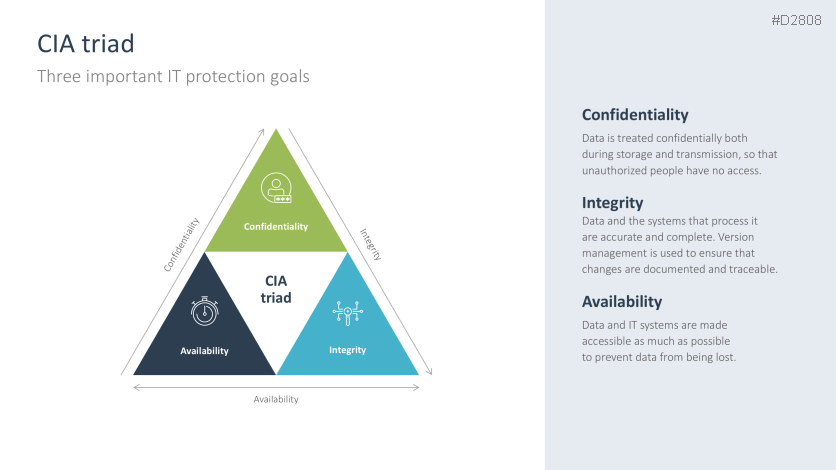
- CIA triad
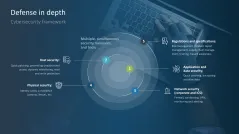
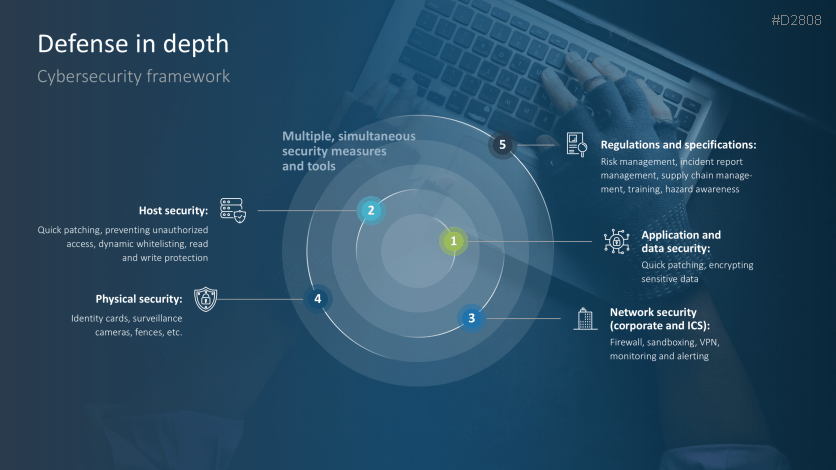
- Defense in depth
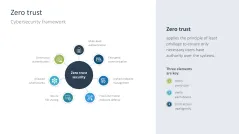
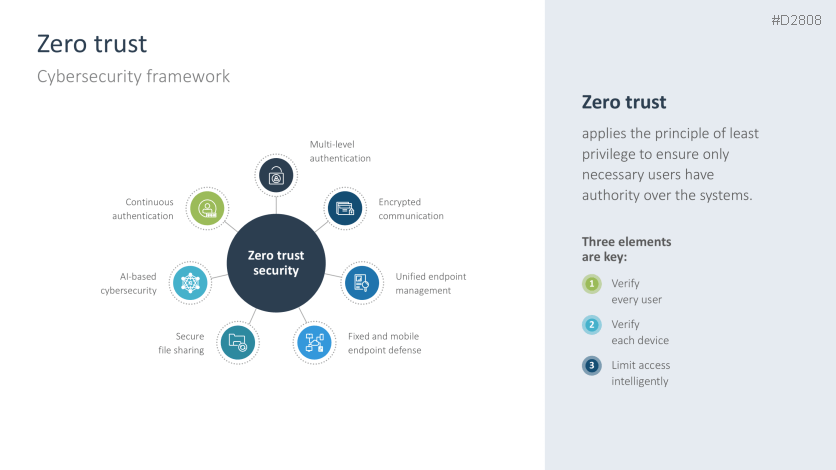
- Zero trust
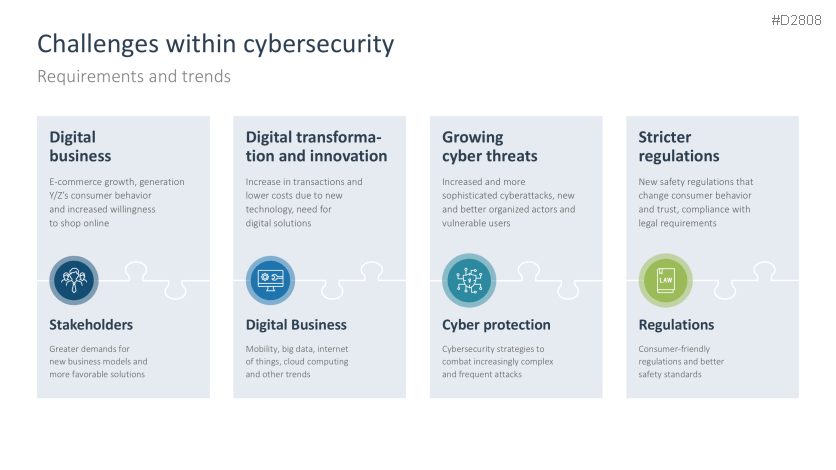
- Challenges within cybersecurity
- Threat landscape
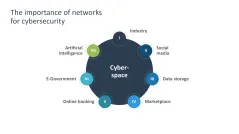
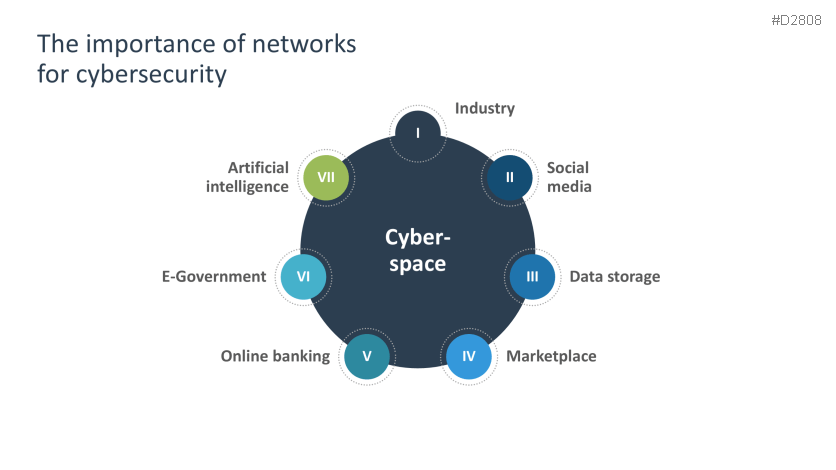
- Network
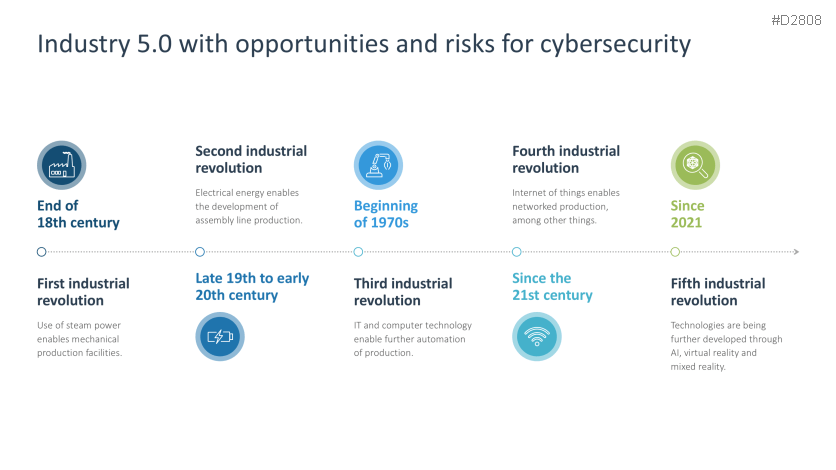
- New industrial developments
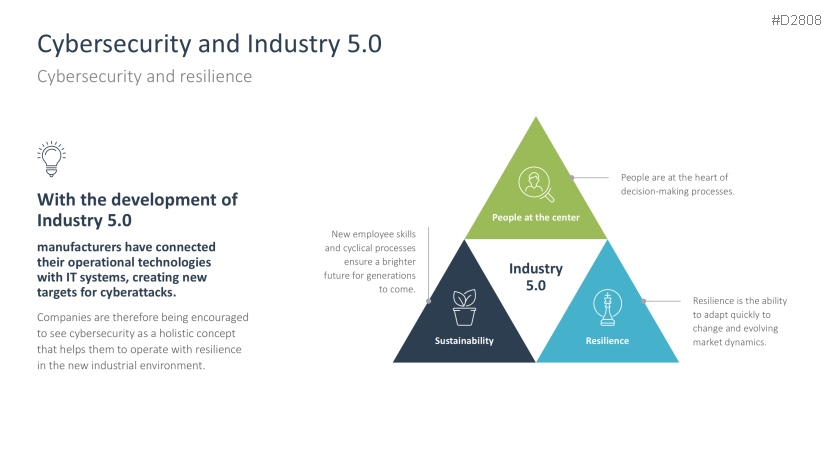
- Cybersecurity and Industry 5.0
- Social media
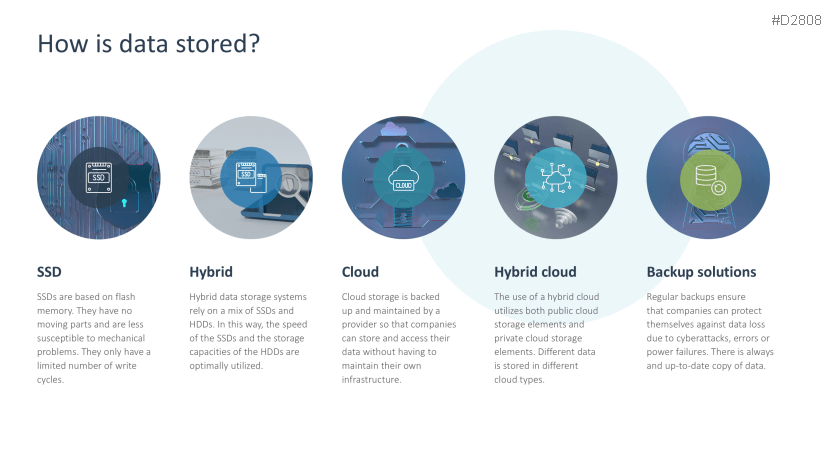
- Data storage
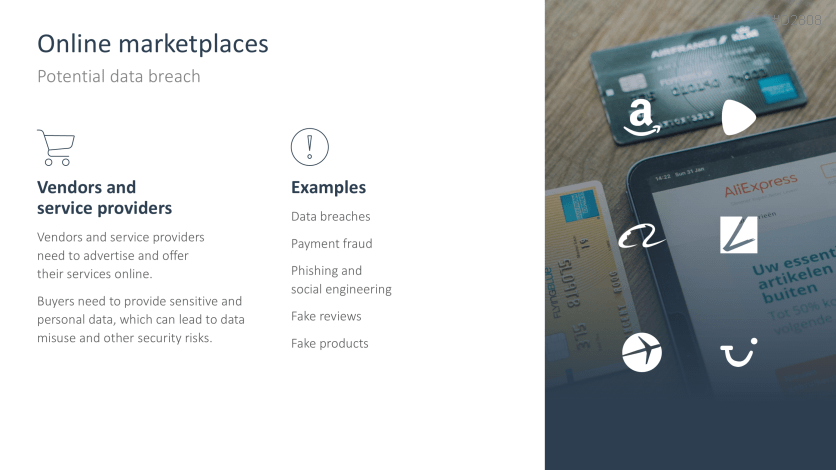
- Online marketplaces
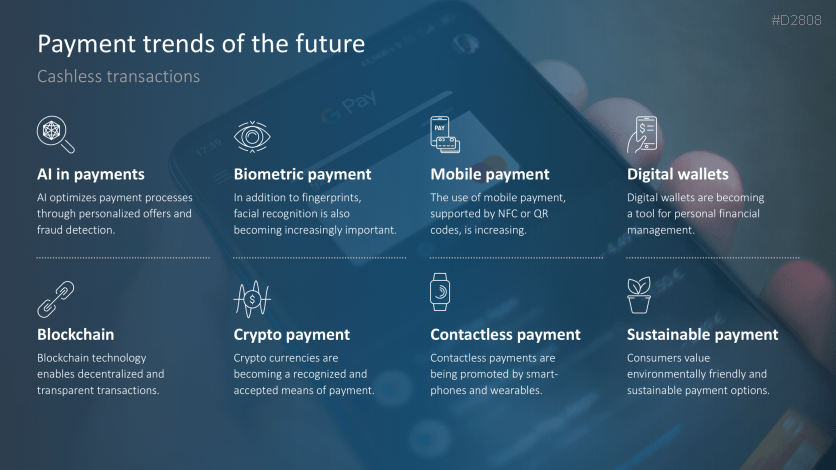
- Banking and cashless transactions
- Politics
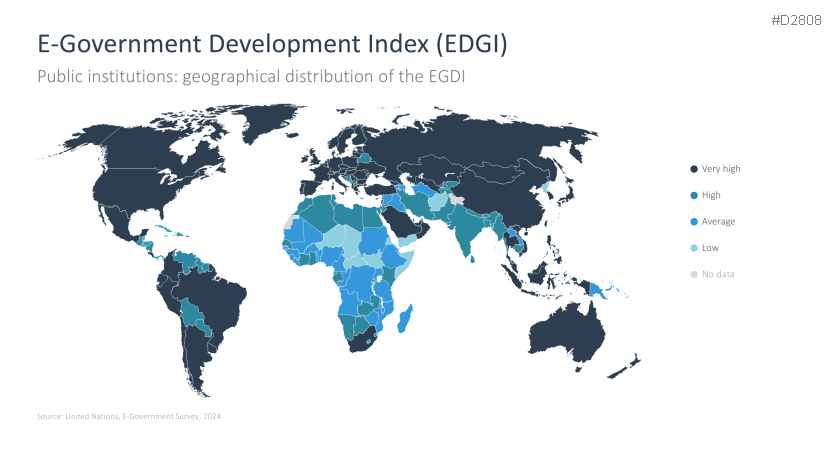
- E-Government Development Index
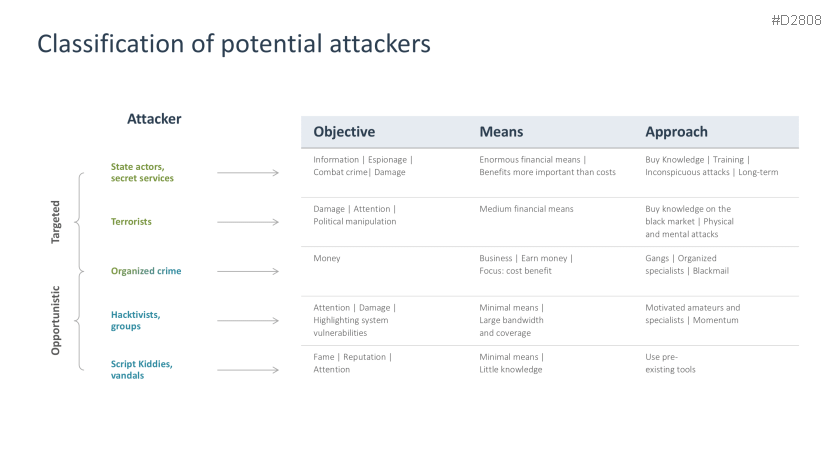
- Potential attackers
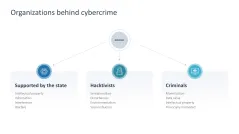
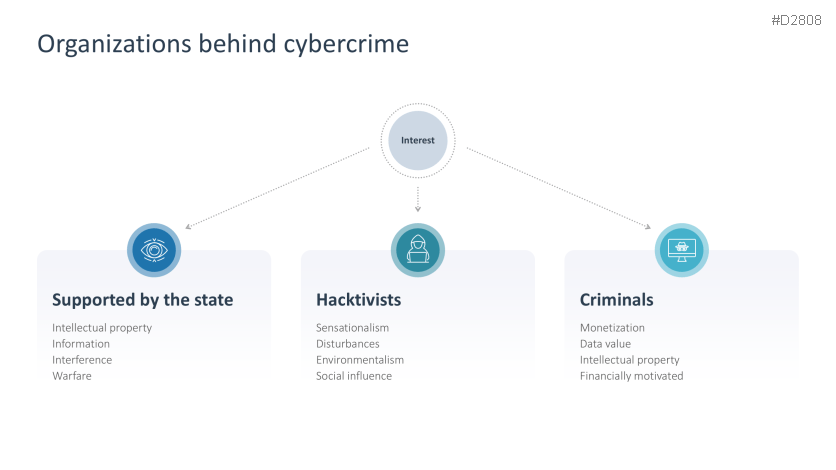
- Cybercrime
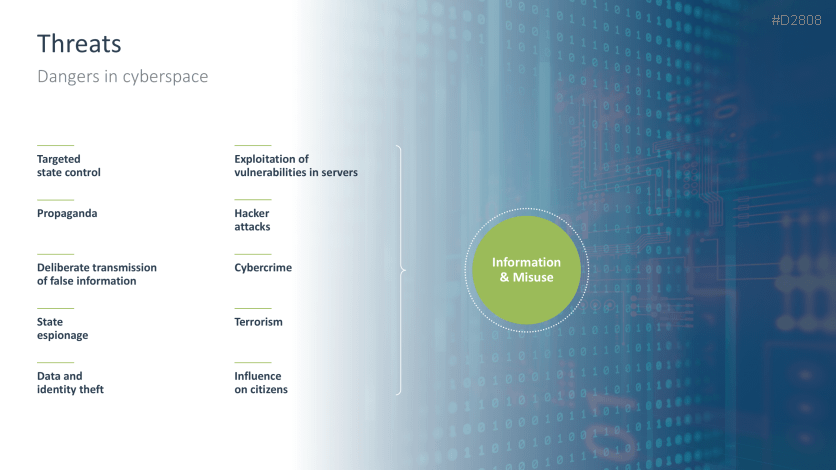
- Threats in cyberspace
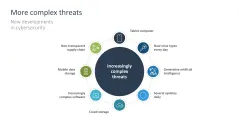
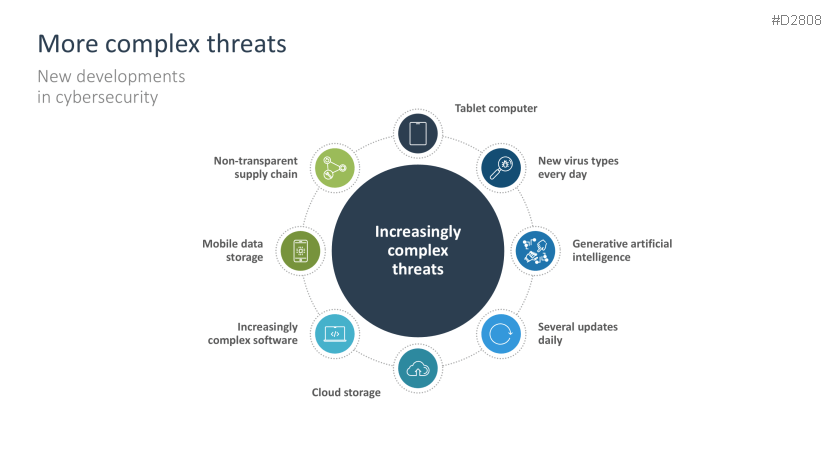
- More complex threats
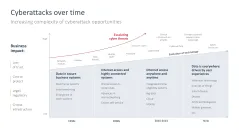
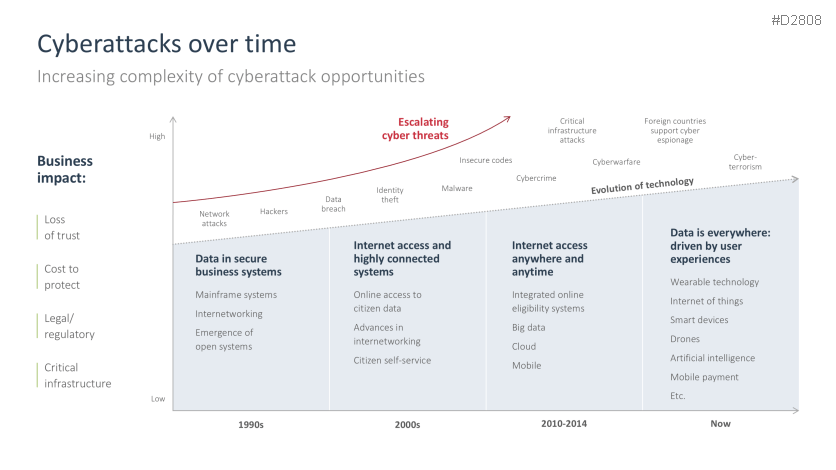
- Cyberattacks: chronology
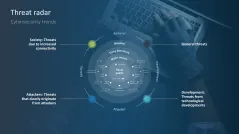
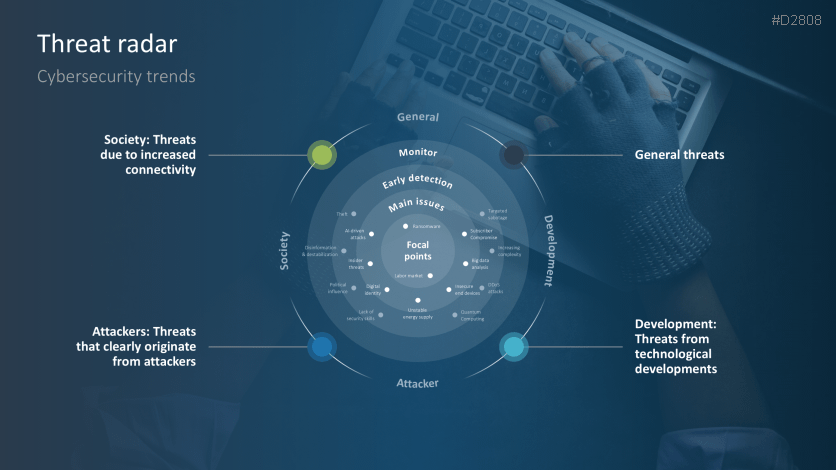
- Threat radar
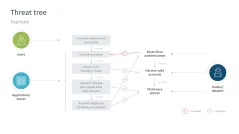
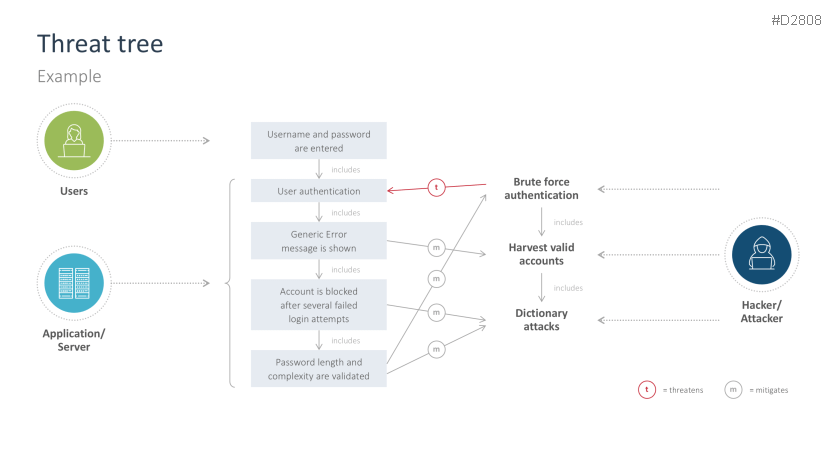
- Threat tree
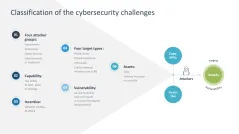
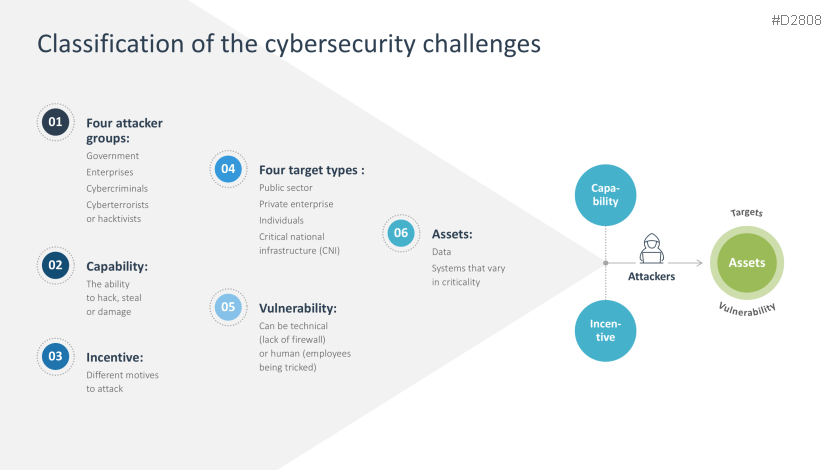
- Classification of cybersecurity challenges
- Cyberattacks and protective measures
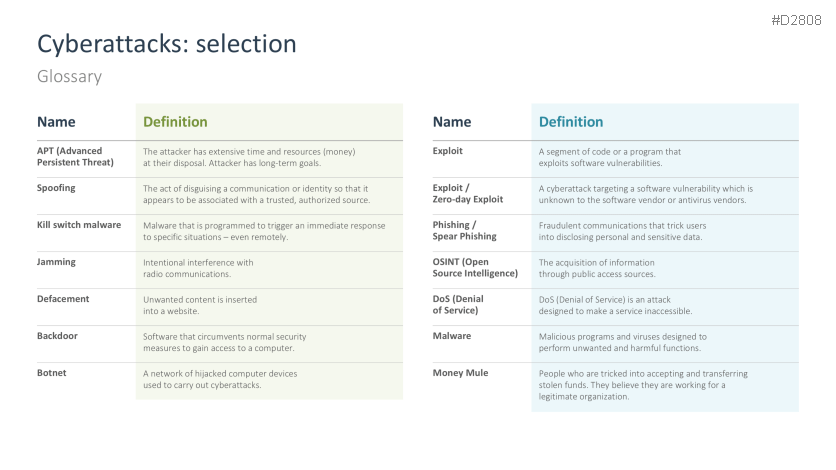
- Cyberattacks: selection
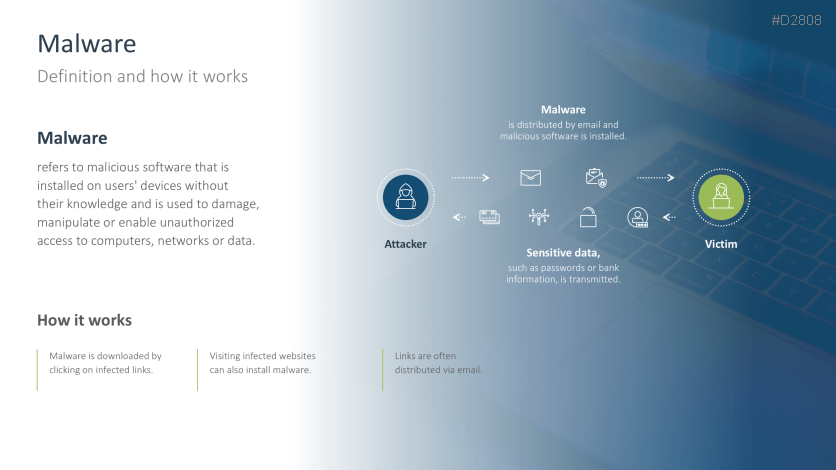
- Malware
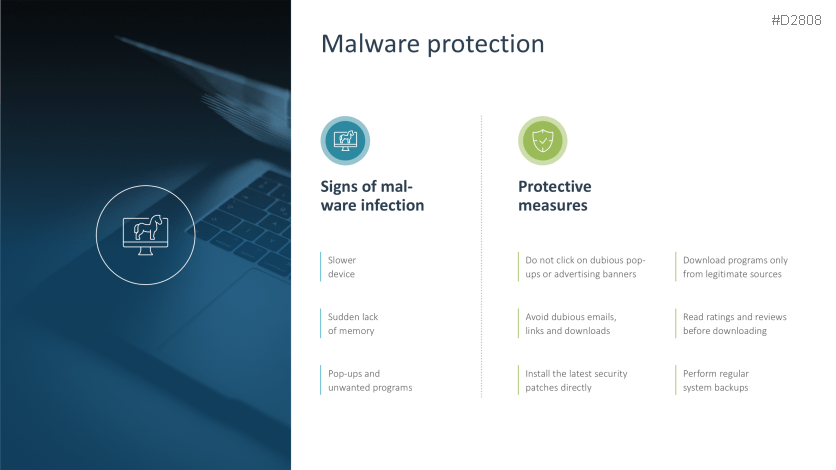
- Malware protection
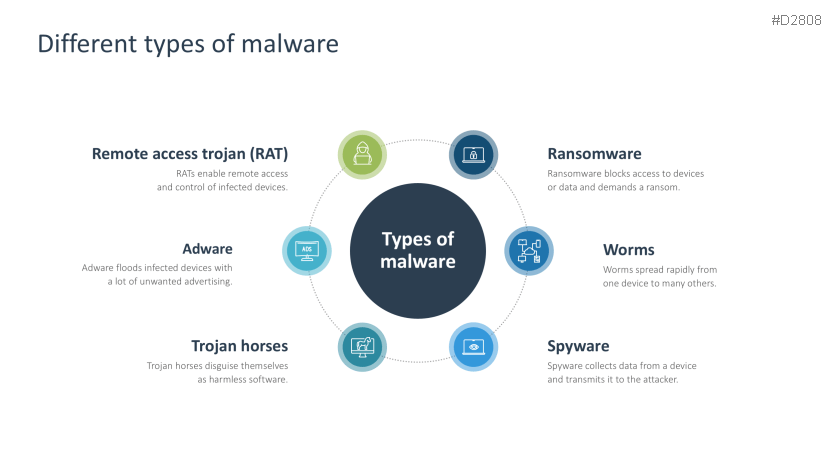
- Different types of malware
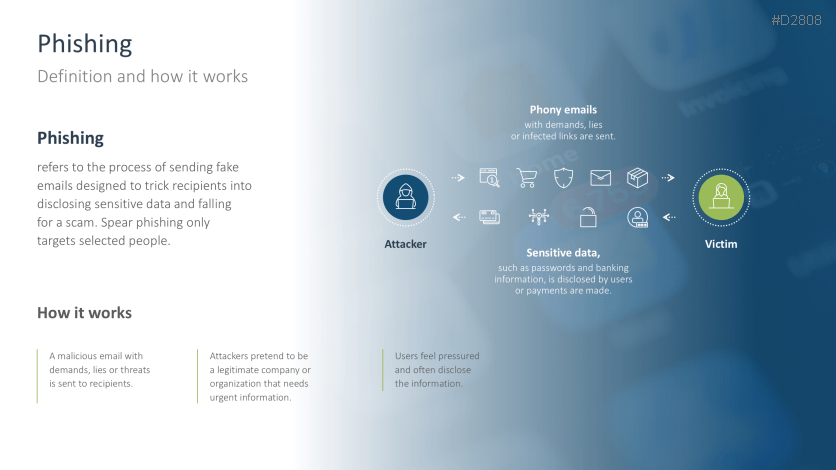
- Phishing
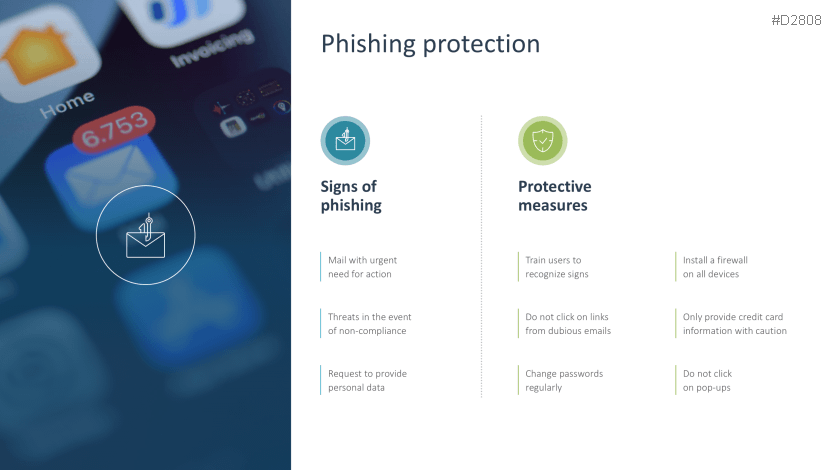
- Phishing protection
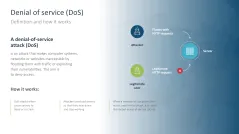
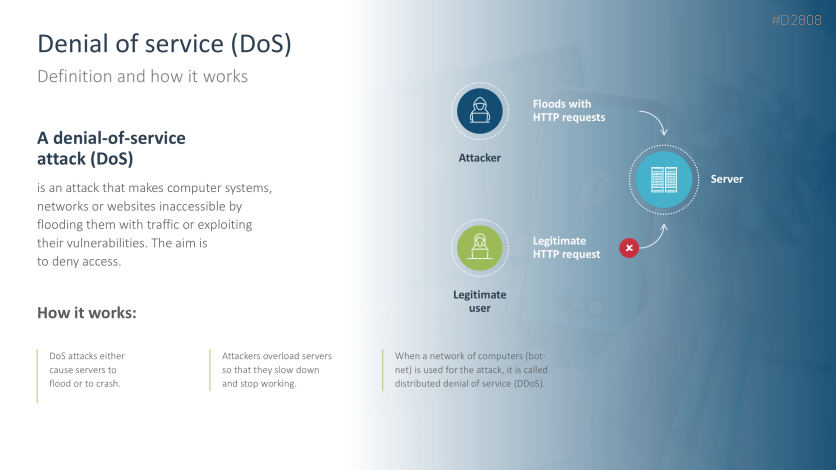
- Denial of service (DoS)
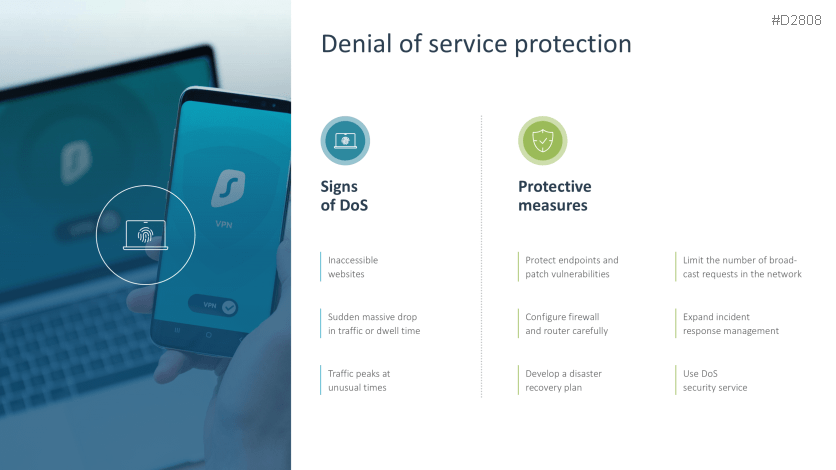
- Denial of service (DoS) protection
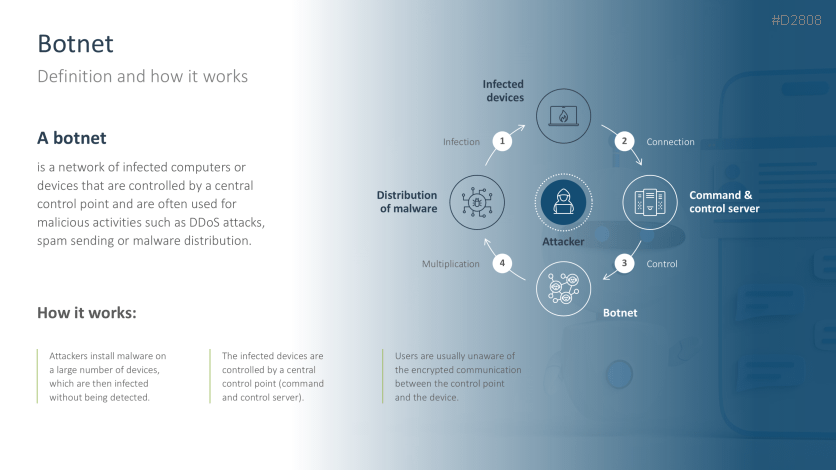
- Botnet
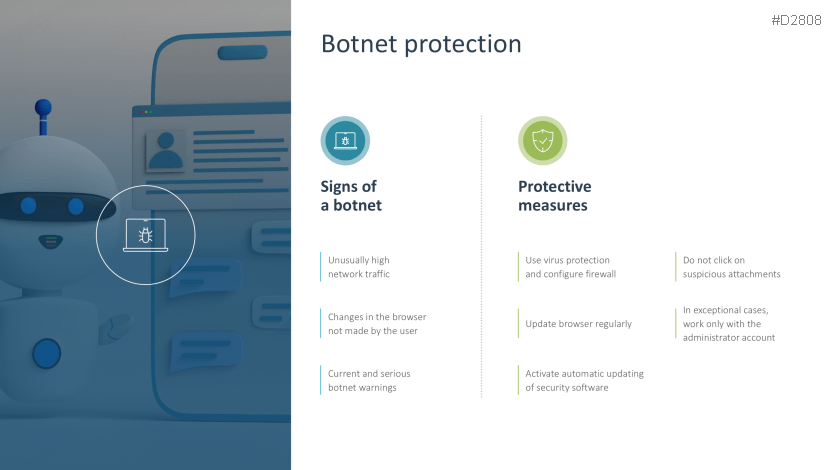
- Botnet protection
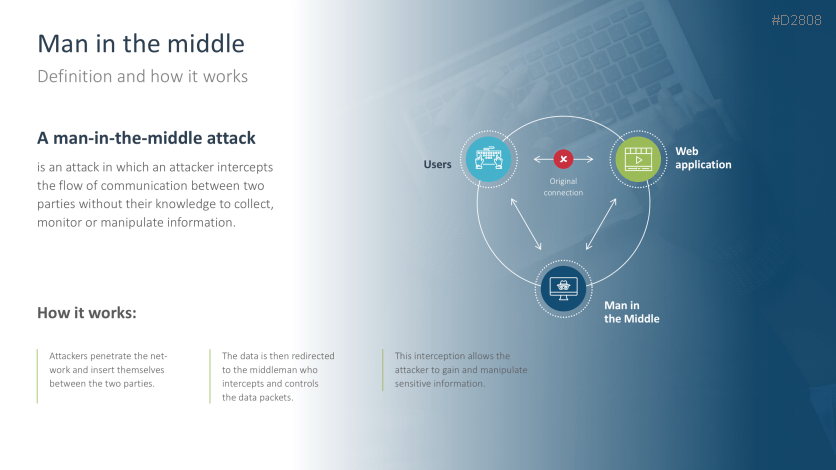
- Man-in-the-middle attack
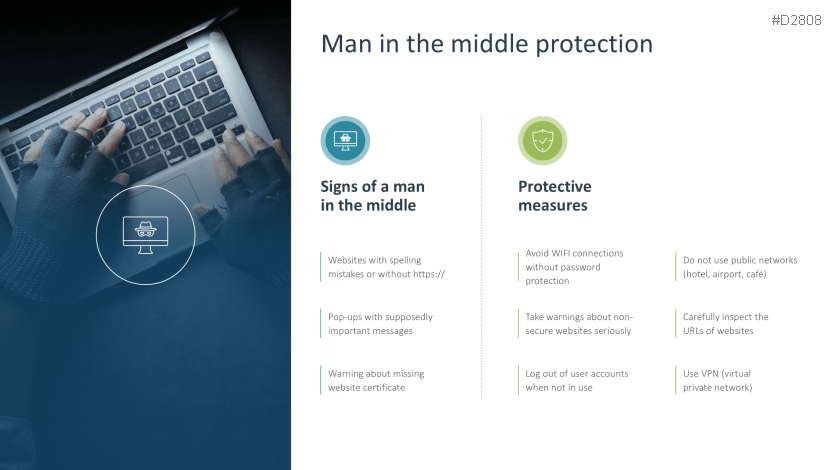
- Man-in-the-middle attack protection
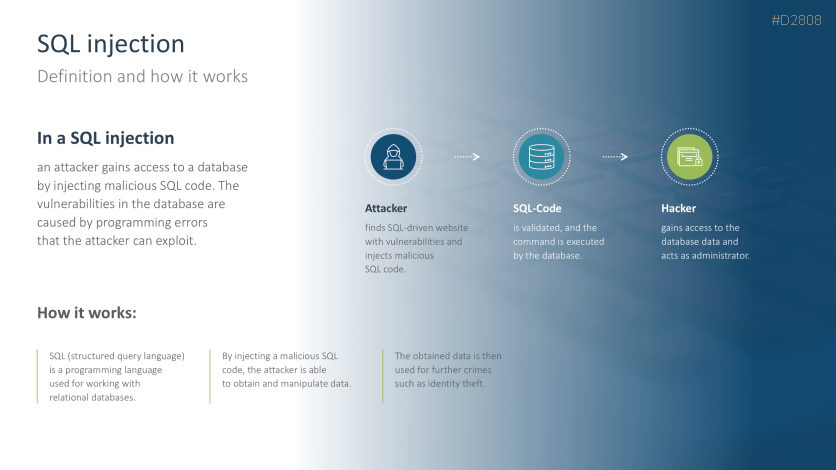
- SQL injection
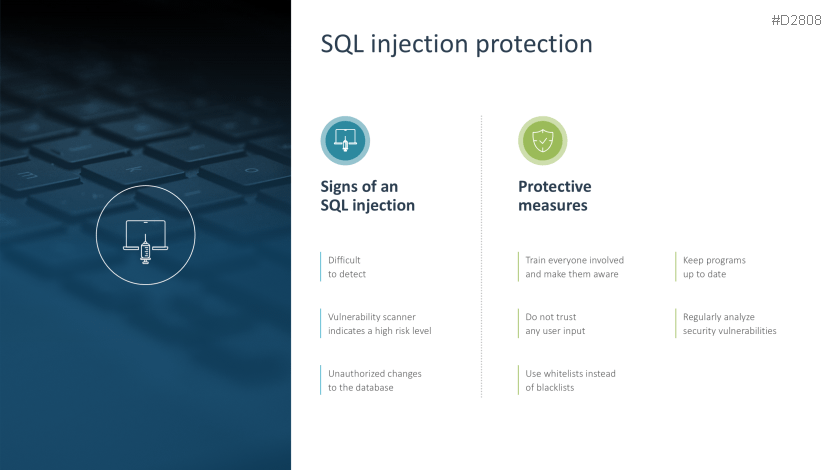
- SQL injection protection
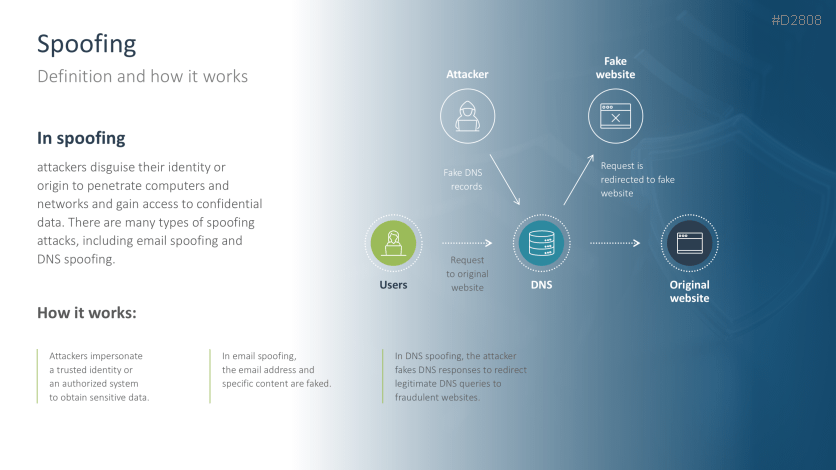
- Spoofing
- Spoofing protection
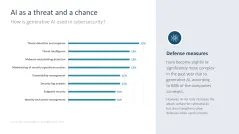
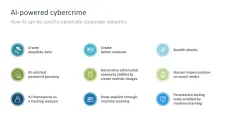
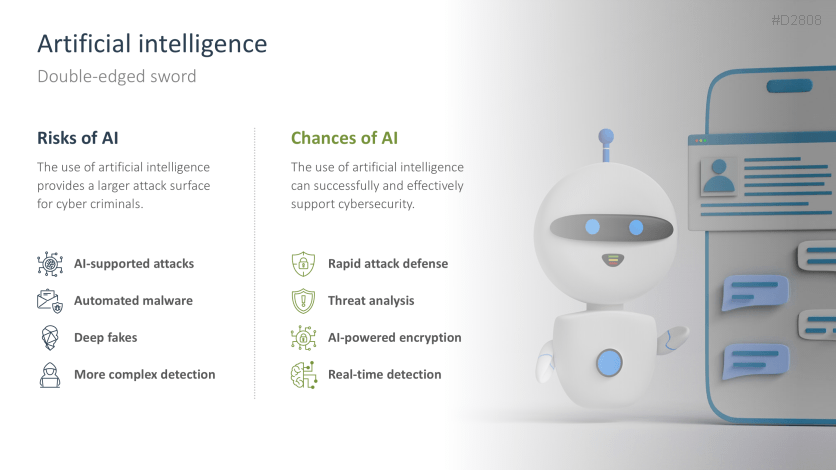
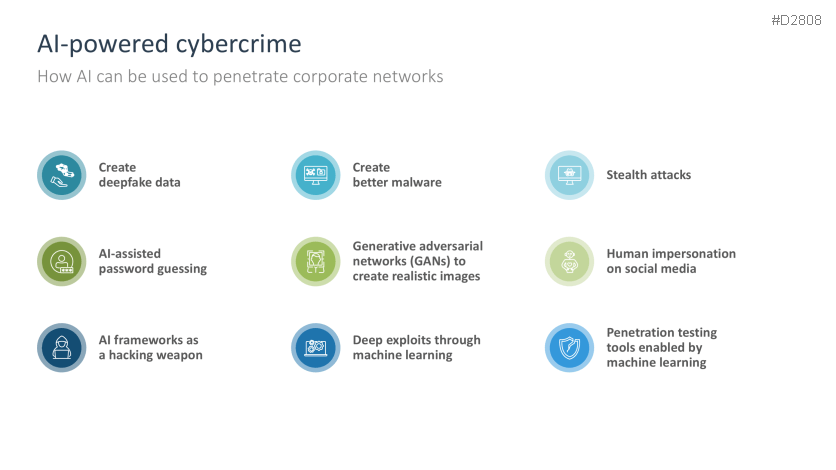
- AI-powered cybercrime
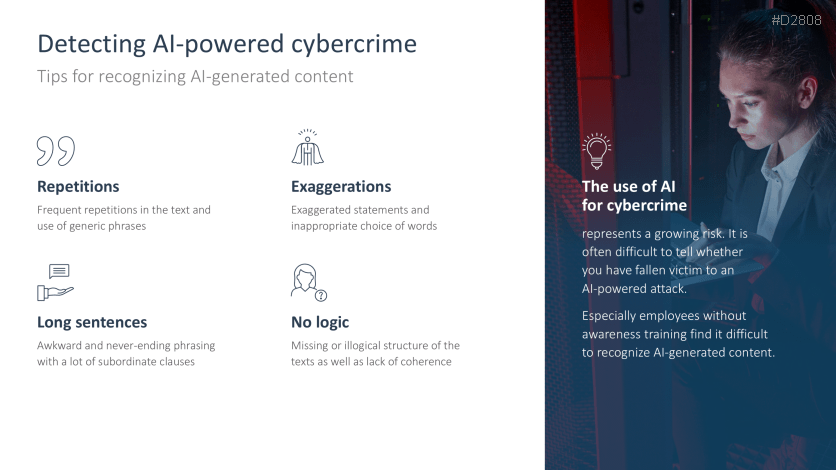
- Detect AI-powered cybercrime
- Defense strategies and tools
- Cybersecurity myths
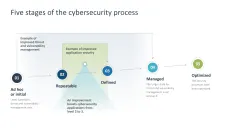
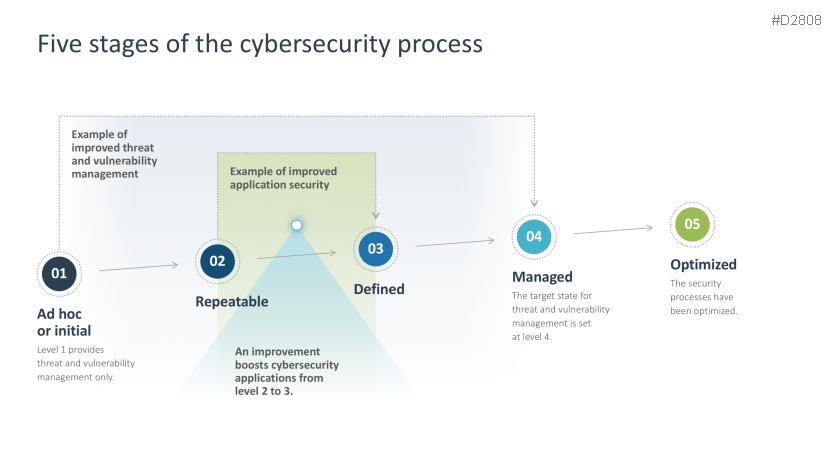
- Cybersecurity process: five steps
- Organizational and technical measures
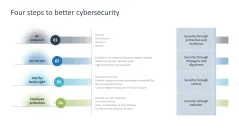
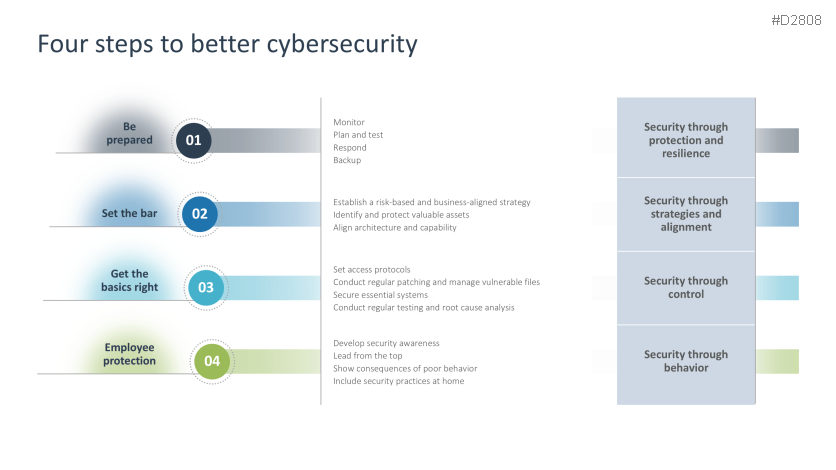
- Four steps to better cybersecurity
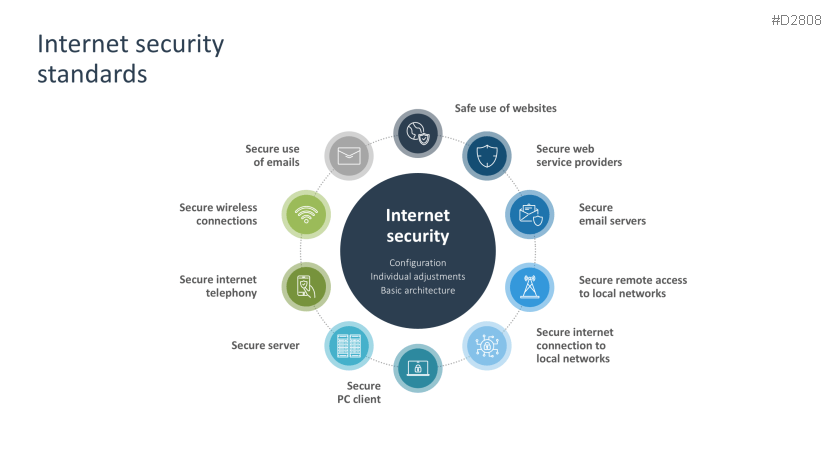
- Internet security standards
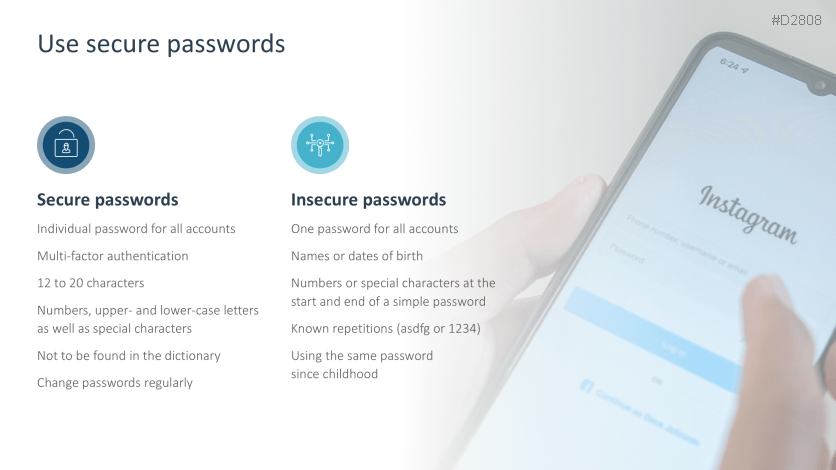
- Password protection
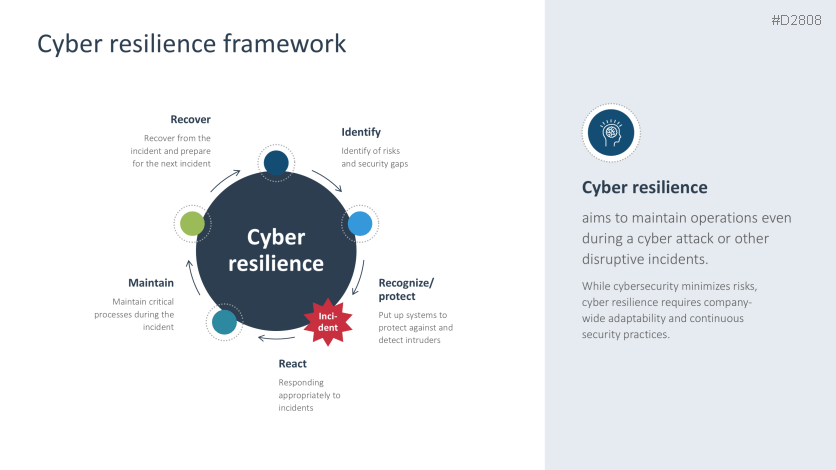
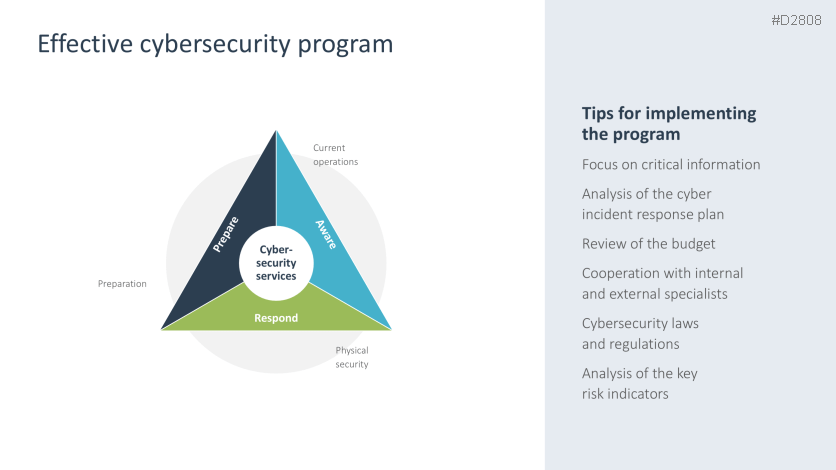
- Effective cybersecurity program
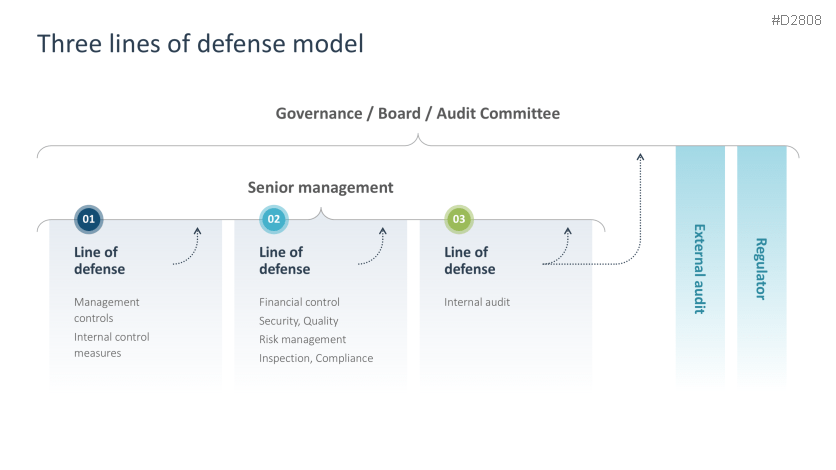
- Three lines of defense model
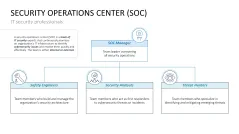
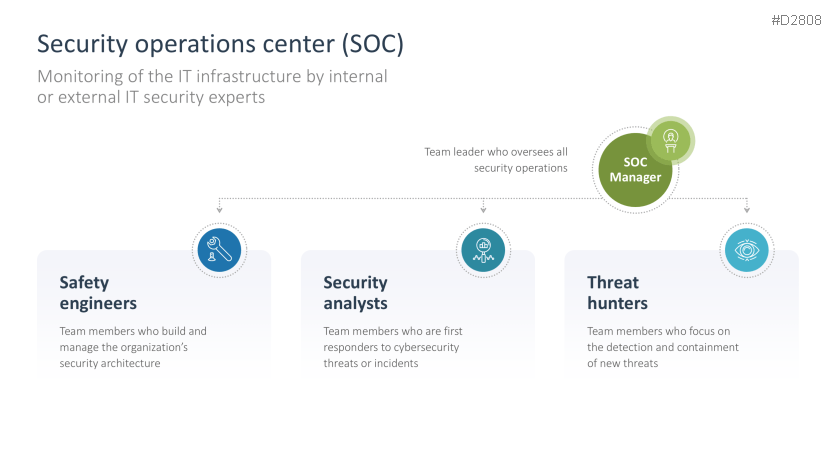
- Security operations center (SOC)
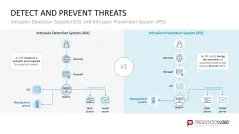
- Intrusion detection system (IDS) and intrusion prevention system (IPS)
- Firewall vs. antivirus
- Incident response plan
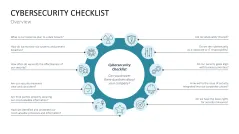
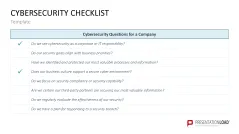
- Cybersecurity checklist
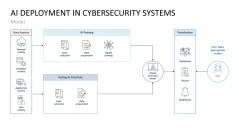
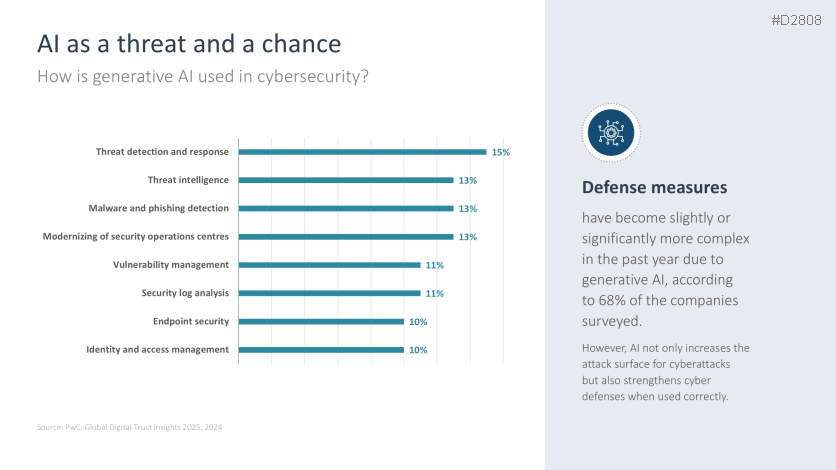
- AI deployment in cybersecurity systems
- Advantages of AI deployment